Connecting state and local government leaders
COMMENTARY | As cities and residents race to become more connected, we must consider how to protect public and private digital property.
Cities face increasing environmental pressures and infrastructure needs, along with growing demands from residents to deliver a better quality of life and to do so at a sustainable cost. Enter the smart city.
Smart cities encourage people to use transit during off-hours, change routes, use energy and water more efficiently, and reduce the strain on the healthcare system through preventive self-care. The result is not only a more livable city, but also a more equitable and productive place for people and businesses to operate.
Los Angeles. Chicago. Boston. New York. Las Vegas. Houston. San Francisco. As of 2018, 11 of the top 50 Smart Cities in the world were U.S. cities. And the number of smart cities continues to grow.
There are two necessary elements in developing a successful smart city that come together to build the necessary connectivity: standardized Wi-Fi and mobile devices.
Personal mobile devices already hold tons of our own and our families’ personal and financial data, as well as company information. As smart city solutions grow and connect with each passerby every day, imagine the amount of data and information found in the phones and apps of smart city residents and businesses.
We protect our personal computers with antivirus, firewalls, VPNs, anti-spyware and every anti-X solution we can find. However, very few people do the same with their mobile devices, and only one smart city has taken the extra step of protecting its residents.
Hackers know this, making the mobile device the easiest attack vector to fully compromise an individual, organization or smart city.
The overwhelming majority of attacks—by our estimates, over 90%—start with the most used feature on a mobile device: the Wi-Fi connections. Unfortunately, Wi-Fi relies on mostly insecure protocols and standards, making them easy to impersonate or intercept, mislead and redirect traffic. When residents set their phone or laptop to automatically use the open WiFi at your local coffee shop, an airport, your cable-slash-telecom company or a major chain restaurant, there’s a good chance they could end up prey to hackers looking to monitor their online activity, or worse.
Most individual mobile users are completely unaware their devices are being attacked because there are very few, if any, telltale signs their device has been compromised. However, even the most cognizant users still have reason for concern. Every IoT device using the WiFi infrastructure in the smart city—traffic lights, sensors, public building entry systems and more—is susceptible to an attack.
Every day, our company, Zimperium, detects six hundred million events. We process the most relevant events as network attacks and create what we call the Danger Zone—a real time map that can warn and prevent you from connecting to malicious WiFi networks. We separate these attacks into three types: low, elevated and critical threats.
In addition to your favorite coffee shop, restaurant and retailer offering free WiFi, most smart cities are offering free public WiFi to residents and citizens. Based on data from our mobile security application, zIPS, we are able to see how municipal and other WiFi networks have become a platform to stage an attack.
San Francisco’s public WiFi is straightforward (it's called SFWifi). The number of attacks we identified on this network over the course of the previous year was staggering: 1,619 on low threats and 47 critical threats on SFWifi. Low end threats are only potentially harmful, consisting of techniques attackers use to find possible victims and user proximity to potentially harmful connections. Critical threats, however, are when we know someone is compromising the data coming from the device.
While this is only a fraction of the more than 75,000 WiFi threats we detected through our zIPS users moving through San Francisco (most of these threats are imitating private WiFi providers), it illustrates the risks inherent in building public sector-provided digital services. And, as this data shown is specific to just WiFi attacks, it is conservative (in comparison to all of attacks) since only a percentage of the population uses zIPS.
Overall, this map of where we have detected and prevented attacks shows the prevalence of WiFi vulnerabilities and threats to mobile users: red is a critical threat, orange is elevated and yellow is low.
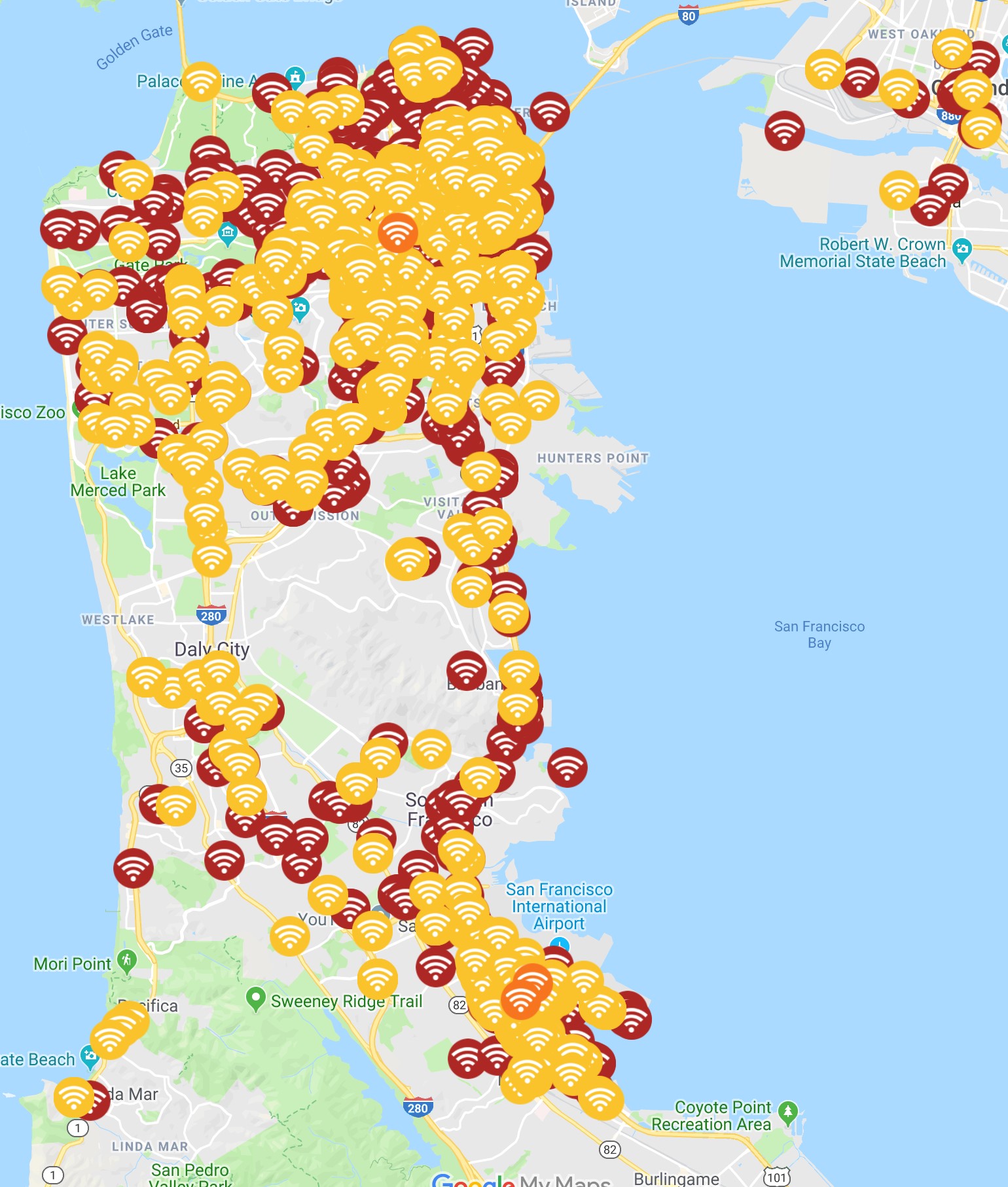
This is a problem that is far from unique to San Francisco: it’s a reality for every modern, connected urban space.
One city has taken action to attempt to resolve the tension between the explosion of “smart city” services and the security concerns of the modern connected city. In July 2017, Mayor de Blasio established New York City Cyber Command, charged with protecting city-owned systems, which deliver critical services to New Yorkers, and helping New Yorkers become safer in their digital lives.
In August 2018, New York City Cyber Command launched NYC Secure, a free smartphone application platform that helps New Yorkers protect their phones against cyber threats by identifying and issuing warnings to users when suspicious activity is detected or they connect to an unsecure Wi-Fi network. Zimperium built the NYC Secure app with the city.
Of note, NYC Secure does not collect or transmit any information to New York City or Zimperium, maintaining trust and individual resident privacy.
Beyond NYC Secure, there are WiFi security solutions available. If adhered to, they will help residents ensure they are connecting to a legitimate WiFi, but will not protect against a host of attack techniques ranging from malware detection to anomalies in processes to phishing attacks to device compromises and malicious profiles. This is why working with the right mobile security solution is your best bet—doing so ensures every person, and therefore the city, is properly protected.
For residents and public sector employees, here are a few things we all can do to prevent these kinds of attacks:
- Configure devices not to automatically connect to known networks. This can be done easily on iOS, but on Android it has to be done for each network. A workaround is to delete known networks periodically.
- Advise users not to connect to open WiFi networks or networks using weak encryption protocols.
- Since users will likely ignore recommendation number two, users should avoid activities involving credentials (email, social media, bank, etc). While hackers will still see the users traffic, it means they won’t capture their credentials (although hackers are still able to perform other kinds of attacks, like directing the user to a malicious website in which the user can be tricked to install malicious apps, etc).
- Use a Virtual Private Network (VPN), which will encrypt traffic and show an attacker a nice set of nonsense characters.
John Michelsen is the chief technology officer at Zimperium.

NEXT STORY: State drone operations on the rise



